A practical guide to using Trezor Suite
The core value of Trezor Suite is that it transforms complex cryptography into clear, repeatable actions. Start by installing the app directly from the official source — Suite is available for Windows, macOS, and Linux. After installation, connect your Trezor device with the included cable. Suite will detect the device and walk you through an initial firmware verification. This verification step is essential: it ensures your device’s software is authentic and hasn’t been tampered with.
When creating a new wallet, Suite will guide you to generate and record your recovery seed. This 12/18/24-word phrase is your backup — write it down carefully and store it offline in a safe place. Avoid photos or cloud backups; treat the seed like a physical key to a vault. If you lose your device, the seed is the only reliable method to restore access.
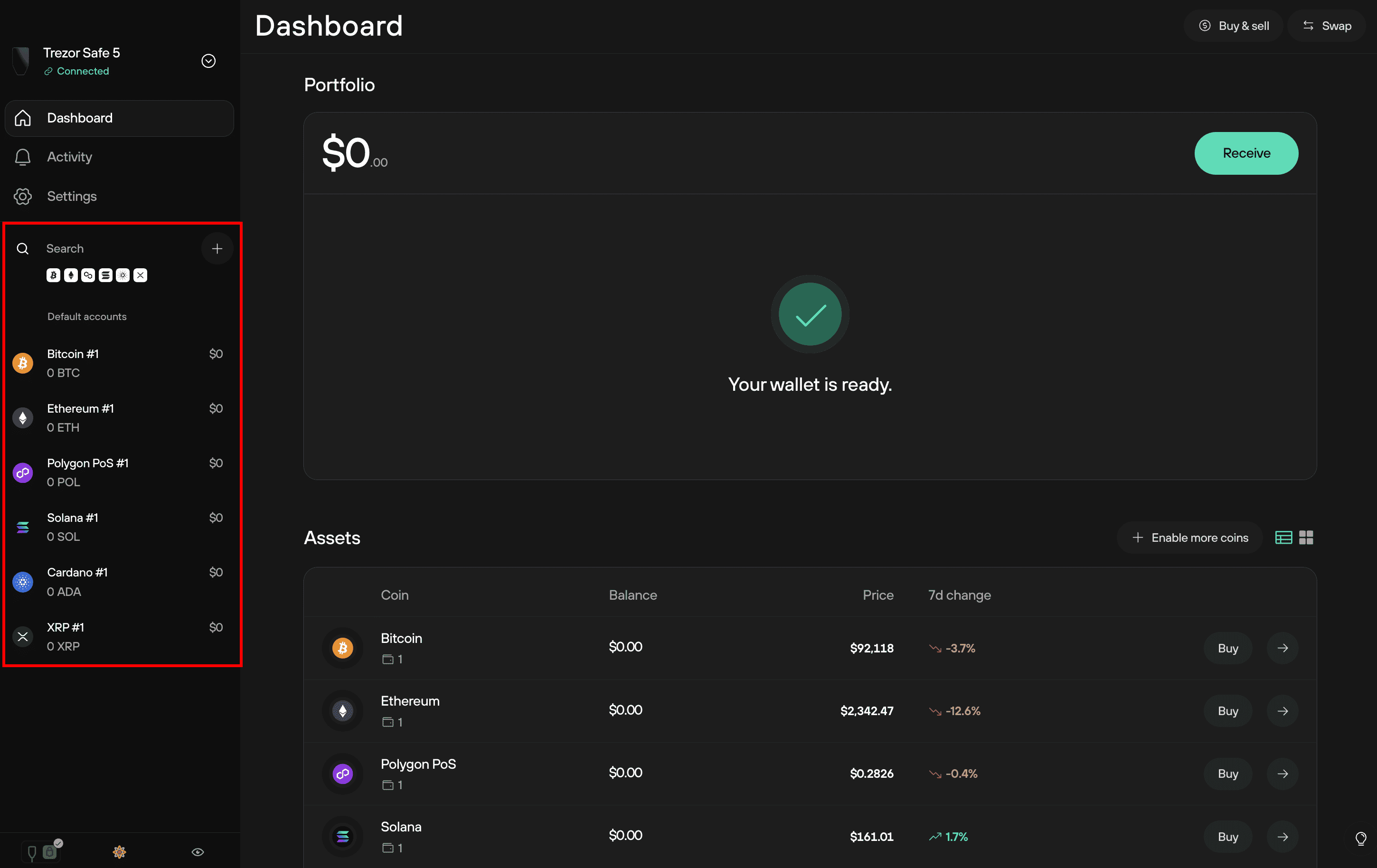
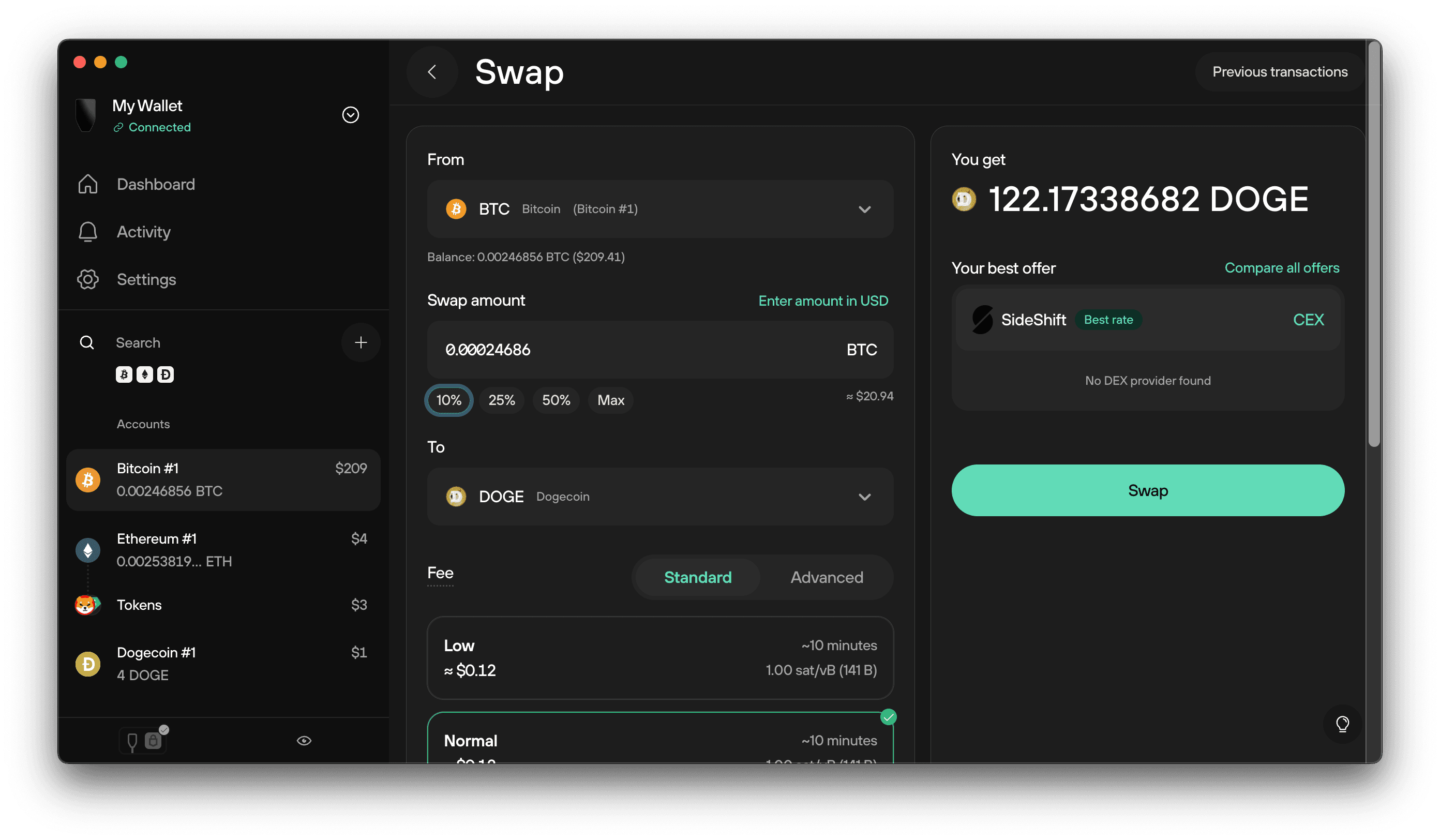
Once set up, using Suite becomes a routine: view your aggregated portfolio, add new coin support, or prepare a transaction. Preparing a transaction in Suite means you choose an output address and fee, then Suite constructs the unsigned transaction. The unsigned payload is sent to your Trezor device which displays exact details — recipient address, amount, and fee — on its screen. You must confirm these details manually on the device. Only after you approve does the hardware sign the transaction and hand it back to Suite for broadcasting. This physical confirmation ensures that an attacker who controls your laptop or browser cannot silently change transaction destinations.
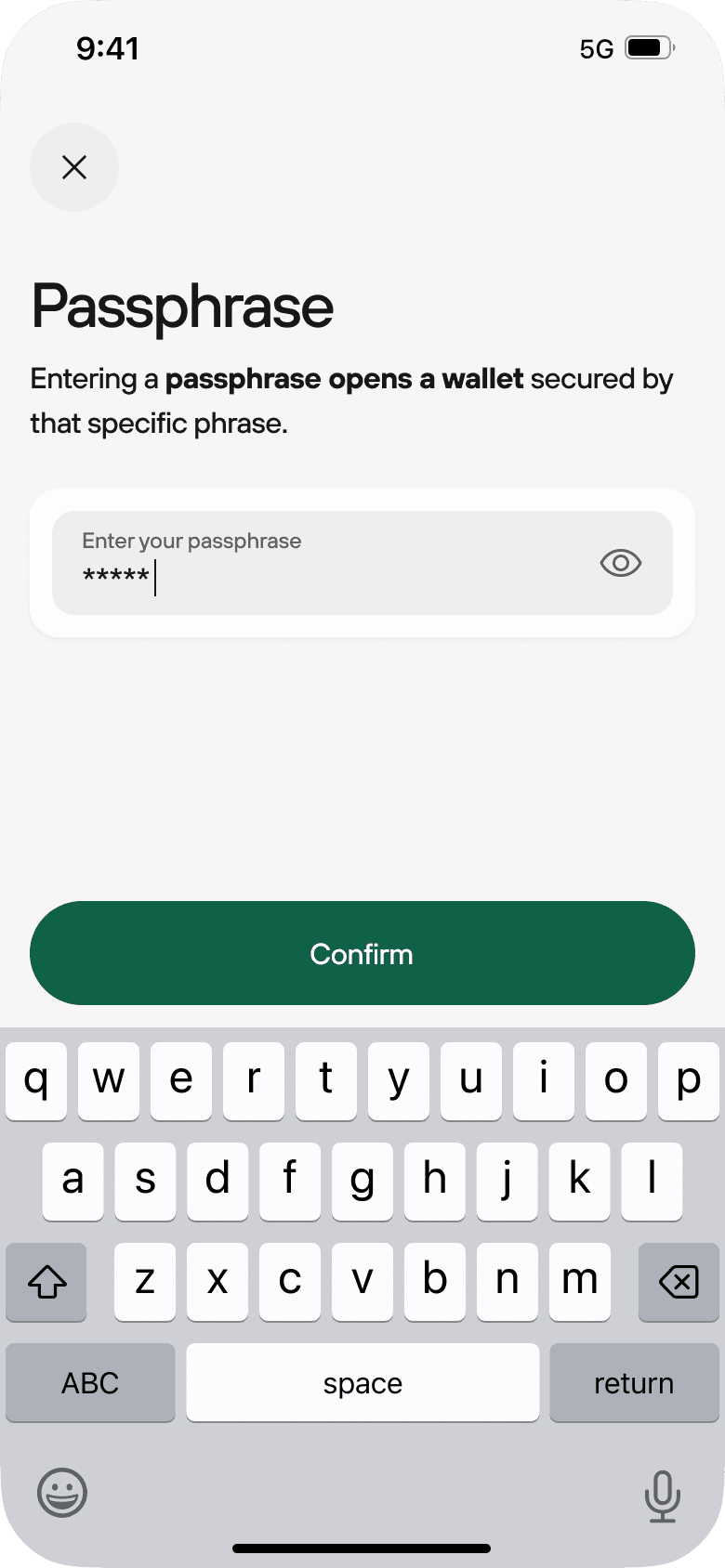
Trezor Suite also helps you stay informed: it provides market data, token metadata, and a clear transaction history. For power users, passphrase-protected accounts enable hidden wallets for additional privacy or compartmentalization. These features paired with Suite’s export tools mean you can analyze transactions, reconcile accounting, or integrate with offline tools without weakening security.
For businesses or users managing multiple devices, Suite supports multi-account workflows and encourages best practices like using dedicated machines for signing, separating high-value cold storage from routine operations, and maintaining physical security for backup seeds. The principle is straightforward: reduce the attack surface while keeping day-to-day operations efficient.
Suite’s design also embraces transparency. The app and device firmware are open for inspection by researchers, and security patches are released regularly. Whenever an update is available, Suite verifies signatures and provides clear prompts about the changes. This auditing model—open code plus signed updates—creates trust and reduces the chance that malicious actors can push unauthorized code to users’ devices.
Practical tips for new and experienced users:
- Always download Suite from the official site and verify checksums when available.
- Record your recovery seed physically and store backups in separate secure locations.
- Consider a metal backup solution for long-term durability in adverse conditions.
- Use a dedicated, updated machine for large transfers if possible.
- Enable optional privacy settings like Tor if you want additional network-level anonymity.
In short, Trezor Suite is designed to reduce friction while preserving the most critical guarantee: that you, and only you, control your cryptographic keys. Whether you are trading occasional small amounts or stewarding a long-term portfolio, Suite provides the visibility, the verification steps, and the workflow tools to manage crypto safely and confidently.